This project contains the demo website and the tools presented in the following blog post : http://blog.gosecure.ca/2016/04/27/binary-webshell-through-opcache-in-php-7
This template parses OPcache files generated by a 32bit platform.
- Download 010 editor
Templates->Open Template...Select OPCACHE_x86.bt- Open your OPcache file
- Press
F5
This tool lets you extract the system_id of a phpinfo() page.
Simply pass a filename or a URL.
$ ./system_id_scraper.py info.html
PHP version : 7.0.4-7ubuntu2
Zend Extension ID : API320151012,NTS
Zend Bin ID : BIN_SIZEOF_CHAR48888
Assuming x86_64 architecture
------------
System ID : 81d80d78c6ef96b89afaadc7ffc5d7ea
This tool lets you disassemble an OPcache file.
You can display it as a syntax tree (-t) or pseudocode (-c). Simply pass a display option and an OPcache file.
$ ./opcache_disassembler.py -c malware.php.bin
#0 $280 = FETCH_IS('_GET', None);
#1 ~0 = ISSET_ISEMPTY_DIM_OBJ($280, 'test');
#2 JMPZ(~408, ->5);
#3 ECHO('success', None);
...
This tool helps detect malware hidden in OPcache files by looking for manipulated OPcache files. It compiles its own version of the source code, compares the compiled file with the current cache file and checks for differences. You must run this tool on the same system as the one where the cache files have been compiled originally.
OPcache malware hunter requires three parameters :
- The location of the cache folder
- The system_id
- The php.ini file used
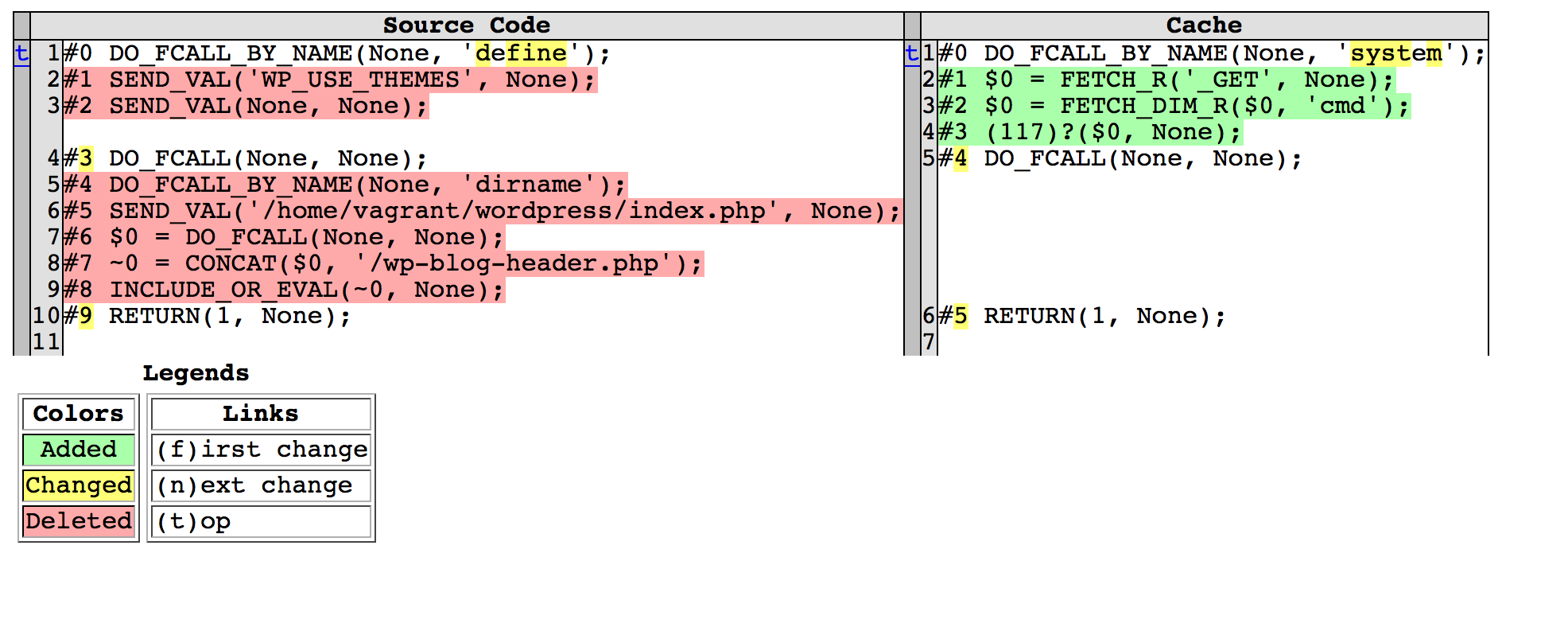
In the situation where a potentially infected cache file is found, OPcache Malware Hunter will generate an HTML report in the filesystem showing the differences between the source code and the infected cache file.
$ ./opcache_malware_hunt.py /tmp/cache 2d3b19863f4c71f9a3adda4c957752e2 /etc/php/7.0/cli/php.ini
Parsing /tmp/cache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/payload.php.bin
Parsing hunt_opcache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/payload.php.bin
Parsing /tmp/cache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/wp-config.php.bin
Parsing hunt_opcache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/wp-config.php.bin
Parsing /tmp/cache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/wp-load.php.bin
...
Parsing /tmp/cache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/index.php.bin
Parsing hunt_opcache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/index.php.bin
Parsing /tmp/cache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/wp-includes/pomo/translations.php.bin
Parsing hunt_opcache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/wp-includes/pomo/translations.php.bin
Potentially infected files :
- /tmp/cache/2d3b19863f4c71f9a3adda4c957752e2/home/vagrant/wordpress/index.php.bin
Main page of generated report :
A typical report page :
To setup the demo, run the following two commands :
sudo ./setup.sh
php -S 127.0.0.1:8080 -c php.ini