badKarma is a python3 GTK+ toolkit that aim to assist penetration testers during all the phases of a network infrastructure penetration testing activity. It allow testers to save time by having point-and-click access to their toolkits, launch them against single or multiple targets and interacte with them through semplified GUIs or Terminals.
Every task's output is logged under a session file in order to help during reporting phase or in a possible incident response scenario. It is also available a proxychains switch that let everything go through proxies, and last but not least, every command can be adjusted before the execution by disabling the "auto-execute" checkbox.
badKarma is licensed under GNU GPL version 3.
The Session file is just a sqlite database, it contains all the information gained during the activity, real-time updated it can be exported or/and imported from badKarma's GUI. By default the database is located inside the "/tmp" directory, this means that you have to save it in a different location before rebooting your computer.
Inside the database there are four tables: hosts, ports, activity_log and notes.
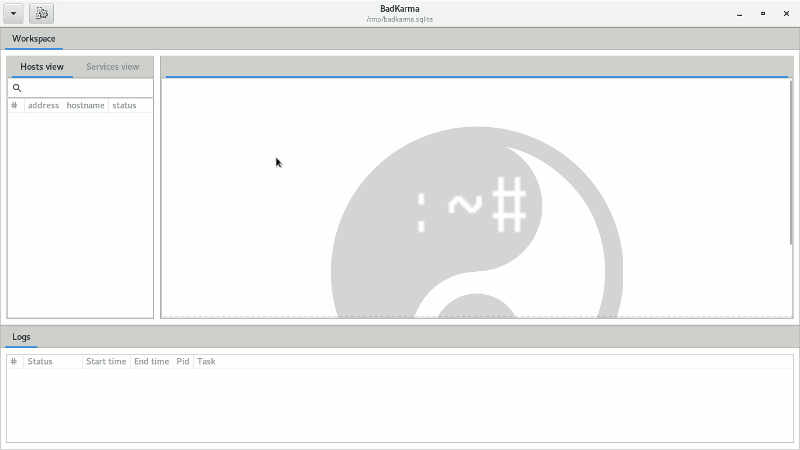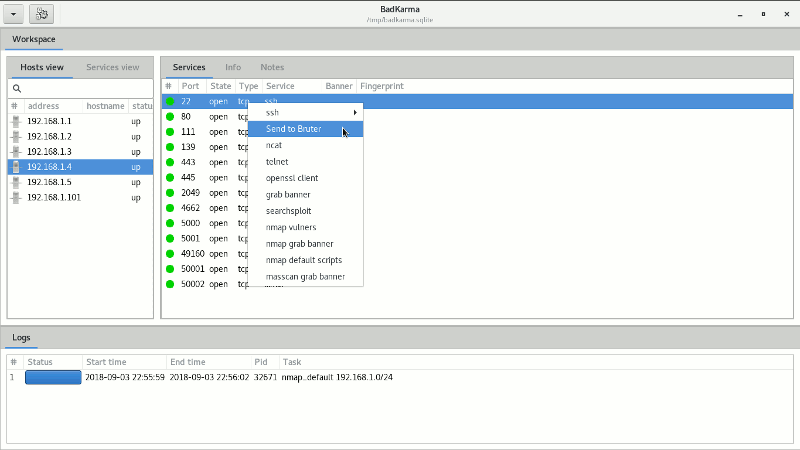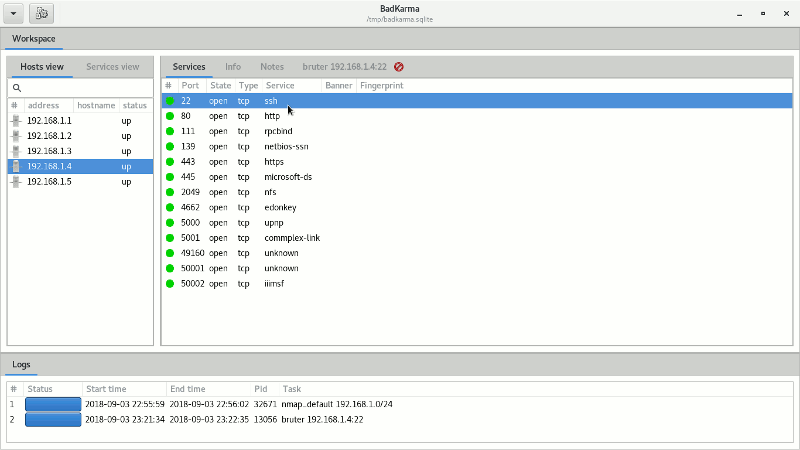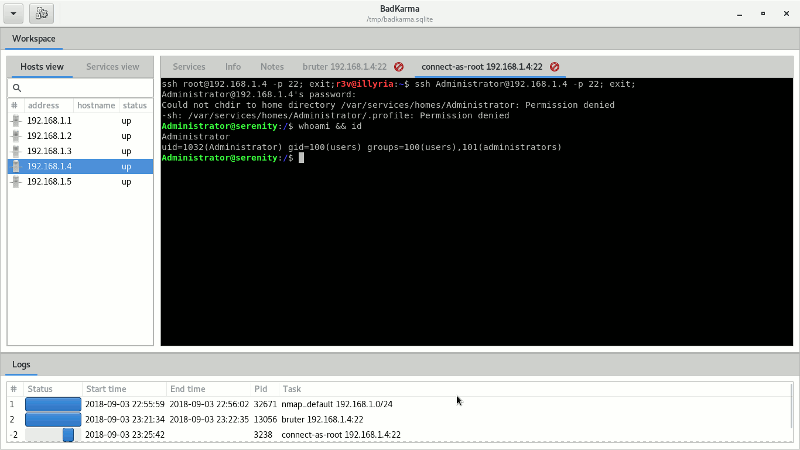
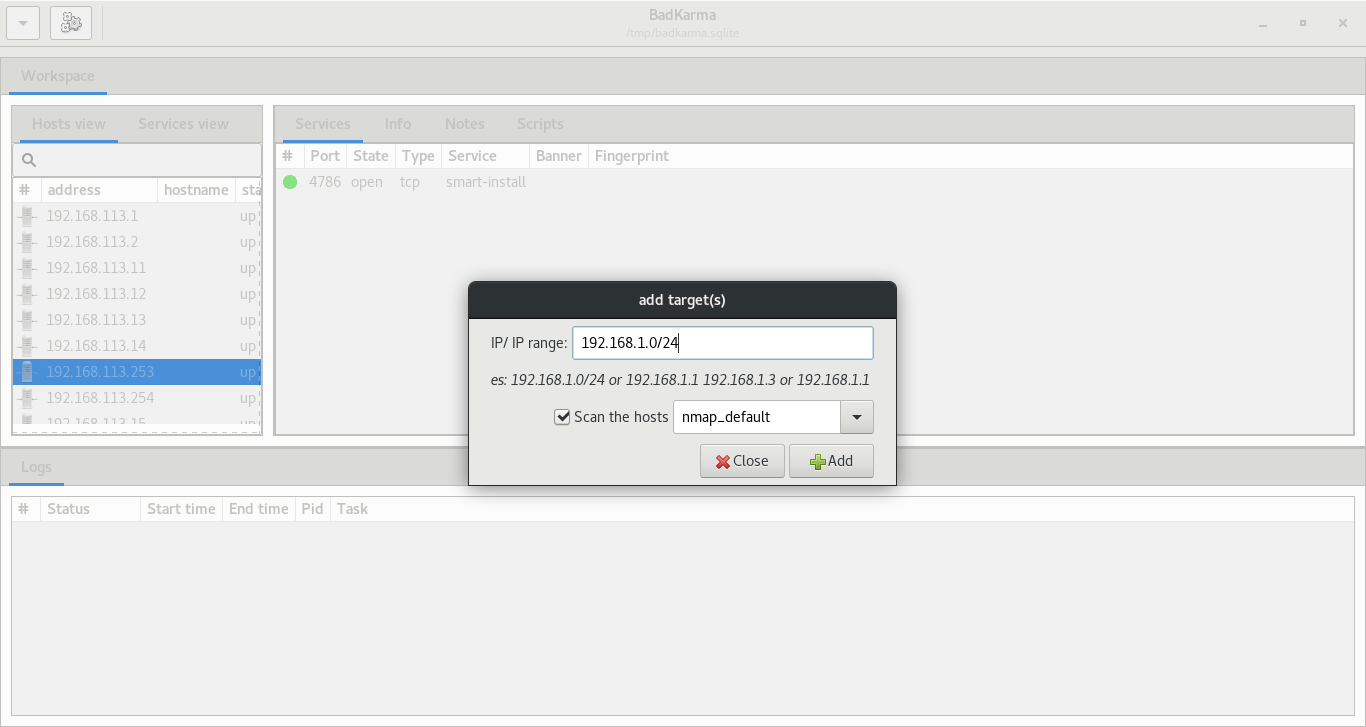
It is possible to add targets and scan them with nmap and/or masscan from the GUI, some defaults scan profiles are already available as well. It is possible to import XML scanners result from the main menu.
There is also a shodan-api's script (smap.py) that let the tester importing target's data directly from shodan. It is located inside the scripts directory and it require a shodan api key inside conf/shodan.conf in order to work.
By default all the scan output are stored inside the "/tmp" directory , then the output is imported in the session file and deleted.
badKarma is modular, the extensions are full-interactive and they allow the penetration tester to tune tasks options, since output is logged under the session file, their output can be exported as a raw txt from the "Logs" tab.
Extensions can be found under the "extension" directory, they are sorted in two categories: importers and workspace. Importers extensions aim to identify tools output files, parse them and import the results into the session file.
Current available workspace's extensions are:
- Shell: this is the main module of the toolkit since it allow the tester to execute preconfigured shell tasks. Shell commands are located under the "conf" directory.
- Bruter: as the name says, bruter is the brute-force extension. It allow the tester to send a target directly to Hydra and configure the parameters through a GUI. Default hydra parameters can be modified from conf/bruter.conf.
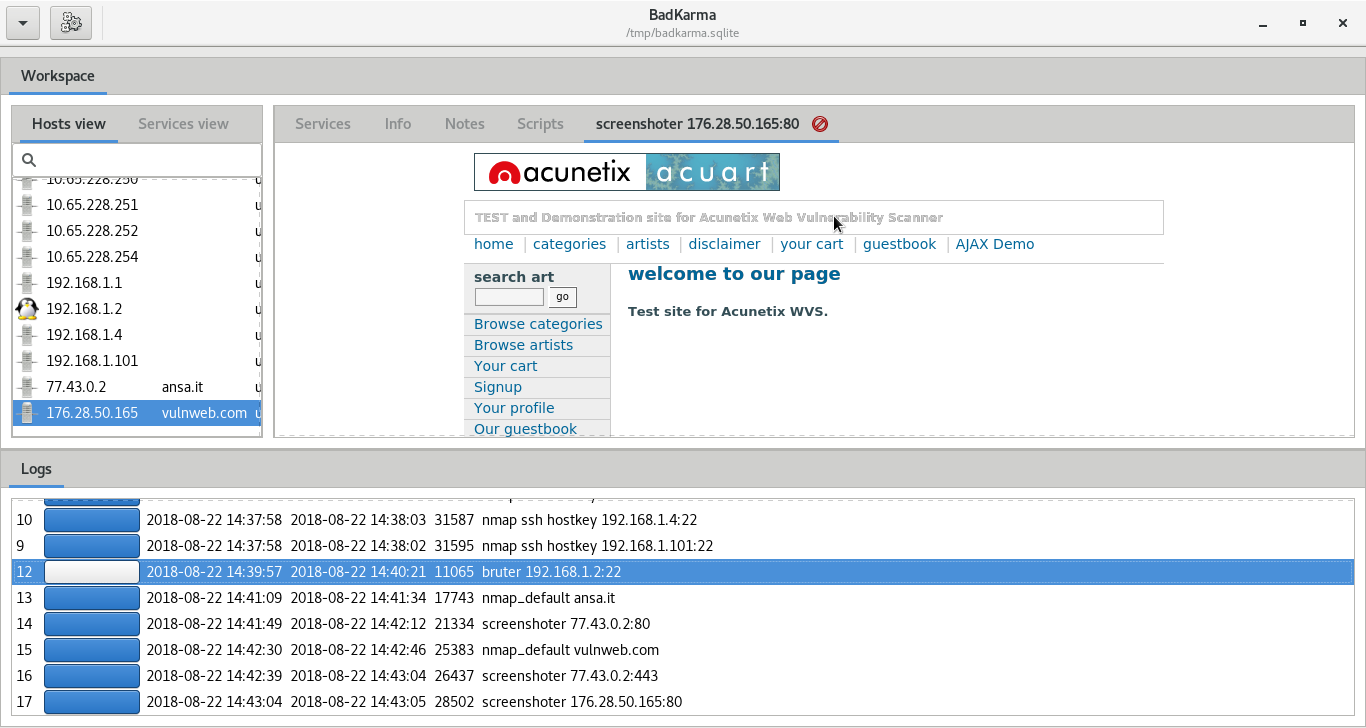
- Screenshot: this extension allow the tester to take screenshots of possibile http,rdp,rtsp,vnc and x11 servers, screenshots will be stored in the session file as base64 and can be shown from badKarma.
- WebSession: a fast and ready to use webview in tailing with mitmproxy, it allow to browse a target's website and read, edit or resend HTTP requests. Some common payloads are available as well, just click on a payload to copy it on the clipboard. Since full dumps are too big to be imported inside the session file, only mitmdump's default ouput is imported.
- Browser: just an "open in browser" for http menu item, take it as an example to build your own extensions.
install Kali linux dependecies:
# apt install python3-pip python3-gi phantomjs mitmproxy ffmpeg gir1.2-gtk-vnc-2.0 \
gir1.2-gtksource-3.0 gir1.2-vte-2.91 gir1.2-osmgpsmap-1.0 gir1.2-webkit2-4.0 clone the repository:
$ git clone https://github.com/r3vn/badKarma.gitinstall python dependecies:
# cd badKarma
# pip3 install -r requirements.txt$ chmod +x badkarma.py
$ ./badkarma.pyIf you appreciated my work, you can buy me a beer via PayPal. I also accept Ƀitcoins to 1Dvvb3TGHRQwfLoUT8rVTPmHqgVjAJRcsm.