Tinfoil Chat (TFC) is a FOSS+FHD messaging system that relies on high assurance hardware architecture to protect users from passive eavesdropping, active MITM attacks and remote exfiltration (=hacking) practised by organized crime and nation state actors.
TFC uses XChaCha20-Poly1305 end-to-end encryption with deniable authentication. The symmetric keys are either pre-shared, or exchanged using X448, the base-10 fingerprints of which are verified via out-of-band channel. TFC provides per-message forward secrecy with BLAKE2b based hash ratchet. All persistent user data is encrypted locally using XChaCha20-Poly1305, the key of which is derived from password and salt using Argon2d. Key generation of TFC relies on Linux kernel's getrandom(), a syscall for its ChaCha20 based CSPRNG.
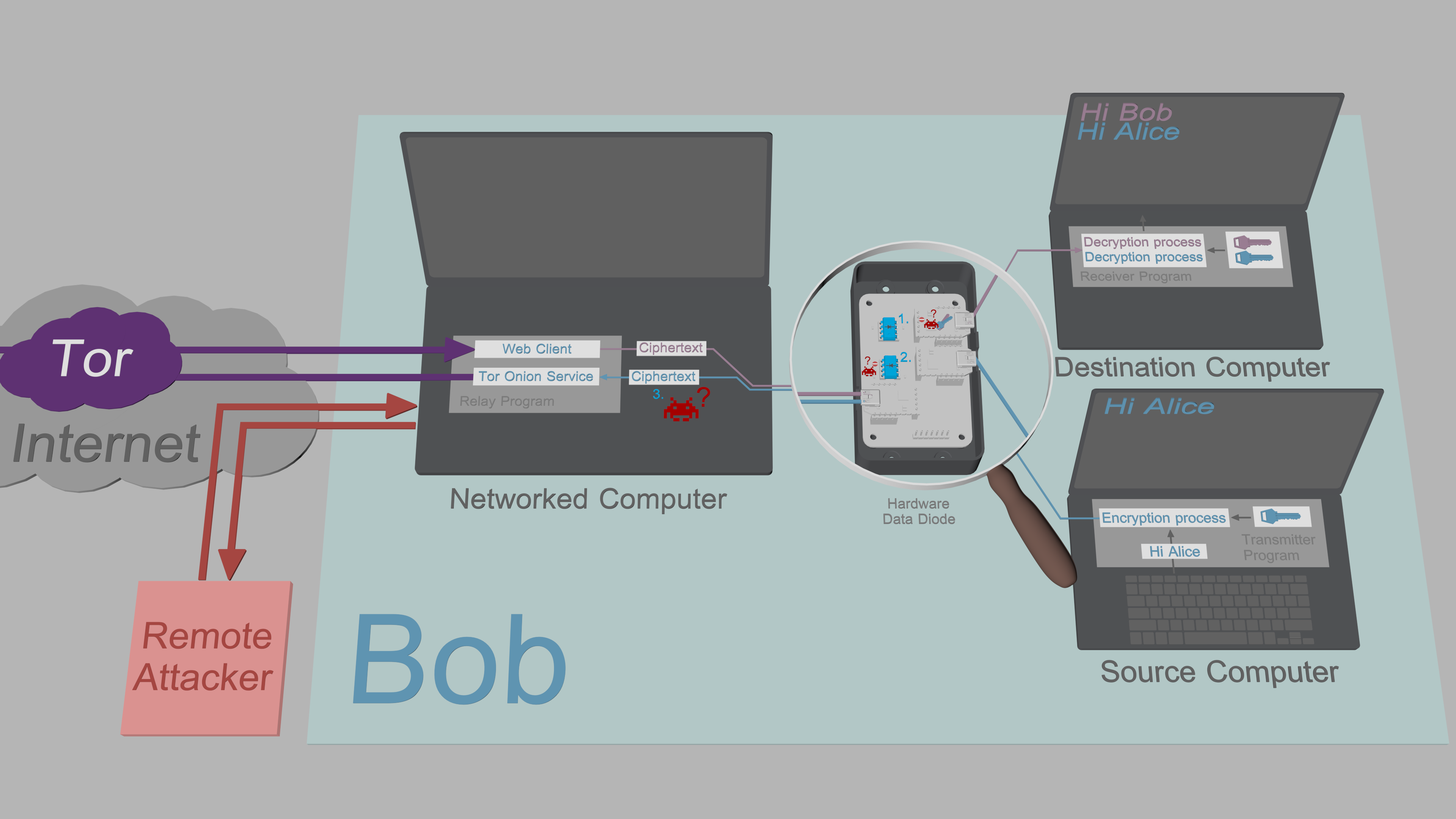
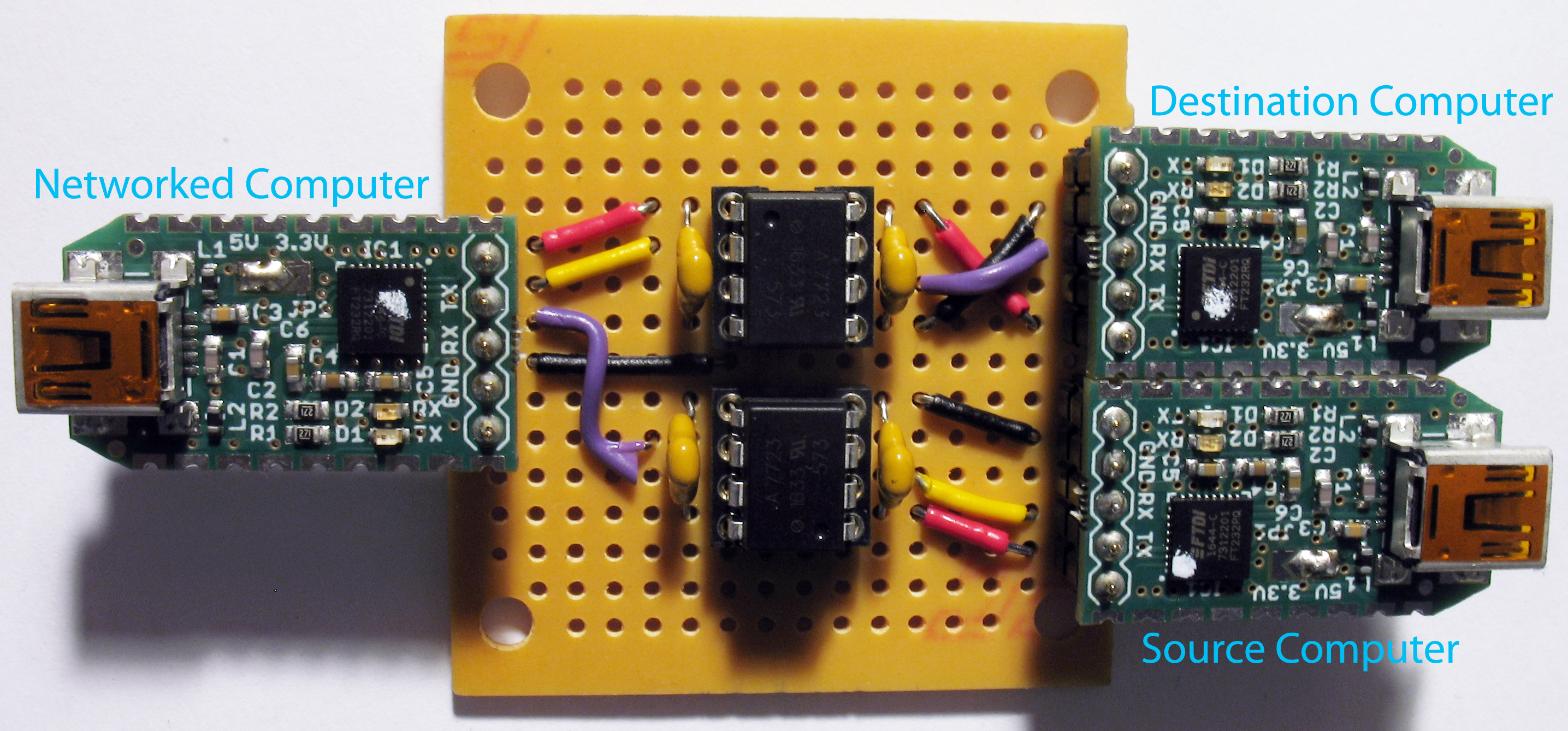
The software is used in hardware configuration that provides strong endpoint security: Encryption and decryption are separated on two isolated computers. The split TCB interacts with a third, Networked Computer, through unidirectional serial interfaces. The direction of data flow between the computers is enforced with free hardware design data diodes, technology the certified implementations of which are typically found in critical infrastructure protection and government networks where classification level of data varies.
TFC routes all communication through next generation Tor (v3) Onion Services to hide metadata about real-life identity and geolocation of users, when and how much they communicate, the social graph of the users and the fact TFC is running. TFC also features a traffic masking mode that hides the type, quantity, and schedule of communication, even if the Networked Computer is compromised.
TFC uses three computers per endpoint: Source Computer, Networked Computer, and Destination Computer.
Alice enters messages and commands to Transmitter Program running on her Source Computer. Transmitter Program encrypts and signs plaintext data and relays the ciphertexts from Source Computer to her Networked Computer through a serial interface and a hardware data diode.
Relay Program on Alice's Networked Computer relays commands and copies of outgoing messages to her Destination Computer via the serial interface and data diode. Receiver Program on Alice's Destination Computer authenticates, decrypts and processes the received message/command.
Alice's Relay Program shares messages and files to Bob over Tor Onion Service. The web client of Bob's Relay Program fetches the ciphertext from Alice's Onion Service and forwards it to his Destination Computer (again through a serial interface and data diode). Bob's Receiver Program then authenticates, decrypts and processes the received message/file.
When Bob responds, he will type his message to his Source Computer, and after a mirrored process, Alice reads the message from her Destination Computer.
TFC is designed to combine the classical and alternative data diode models to provide hardware enforced endpoint security:
-
The Destination Computer uses the classical data diode model. It is designed to receive data from the insecure Networked Computer while preventing the export of any data back to the Networked Computer. Not even malware on Destination Computer can exfiltrate keys or plaintexts as the data diode prevents all outbound traffic.
-
The Source Computer uses the alternative data diode model that is designed to allow the export of data to the Networked Computer. The data diode protects the Source Computer from attacks by physically preventing all inbound traffic. To allow key exchanges, the short elliptic-curve public keys are input manually by the user.
-
The Networked Computer is assumed to be compromised. All sensitive data that passes through it is encrypted and signed with no exceptions.
Optical repeater inside the optocouplers of the data diode (below) enforce direction of data transmission with the fundamental laws of physics.
- *buntu 19.04 (or newer)
- Tails (Debian Buster or newer)
- *buntu 19.04 (or newer)
Threat model
FAQ
Security design
Hardware
Data diode (breadboard)
Data diode (perfboard)
For the rest of the articles, see TFC wiki.