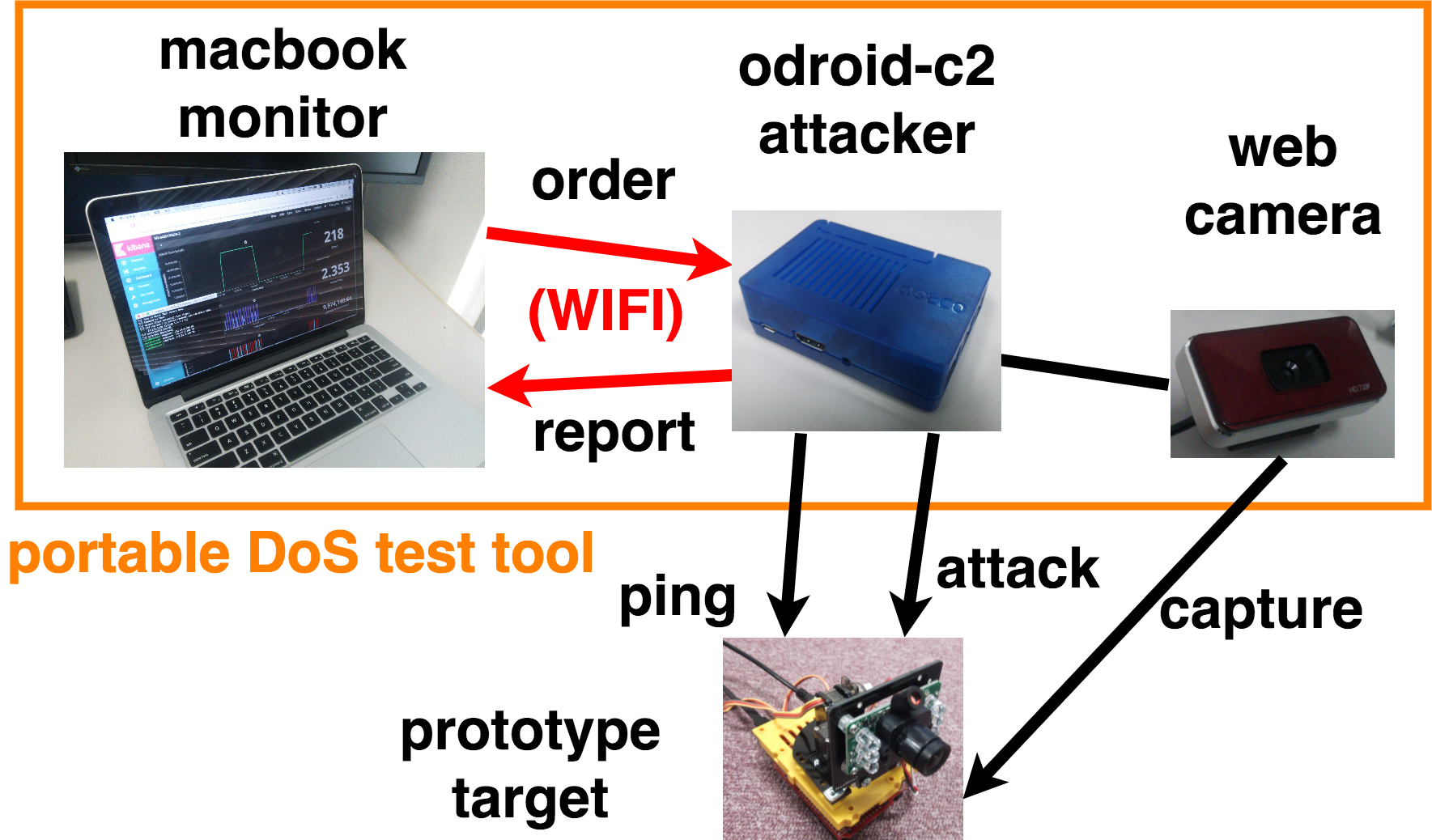
This DoS tool consists of the monitor and the attacker.
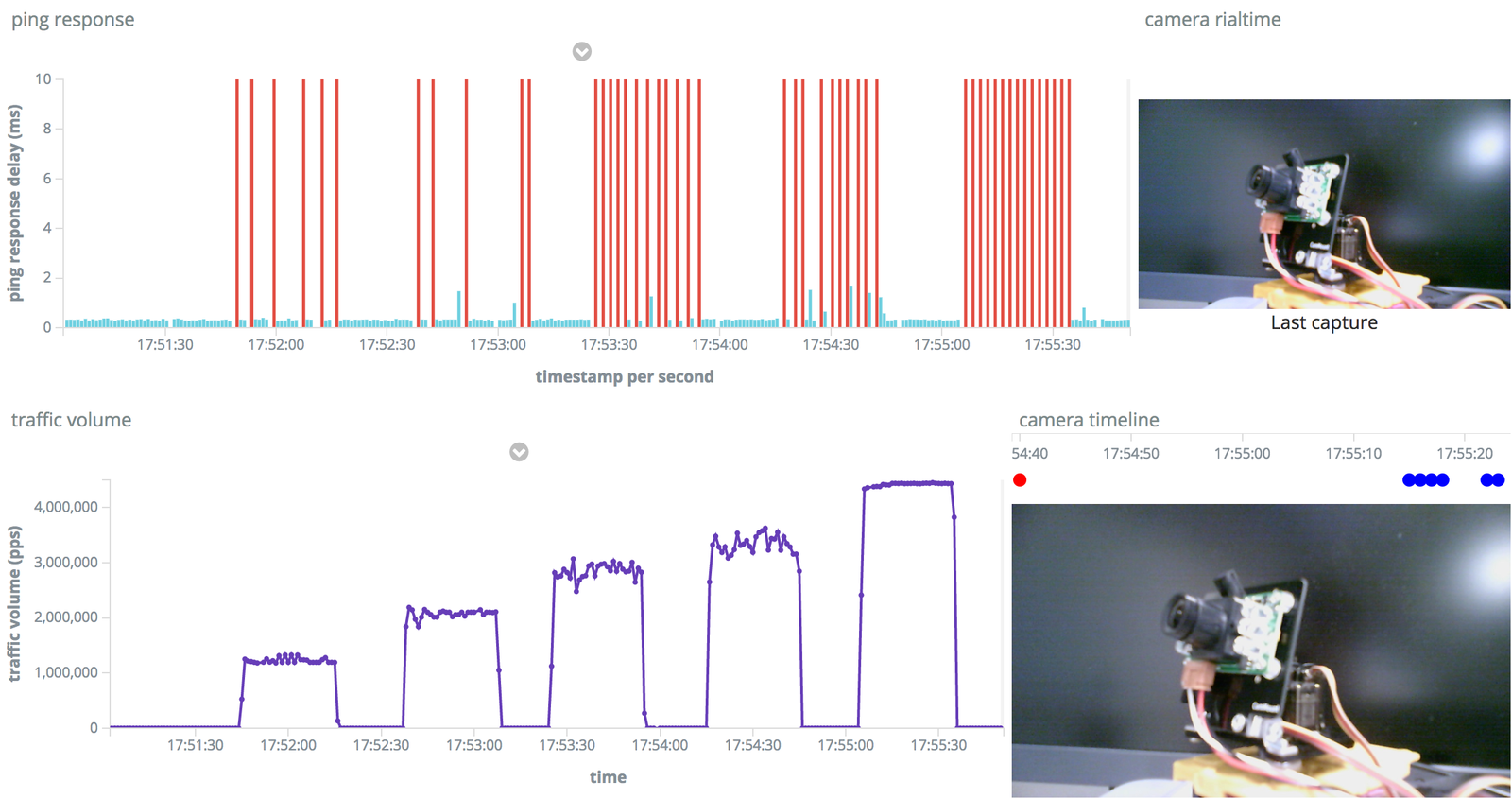
The portable DoS tool monitor is instructs the attack and visualizes the load.
The attacker tool is available here.
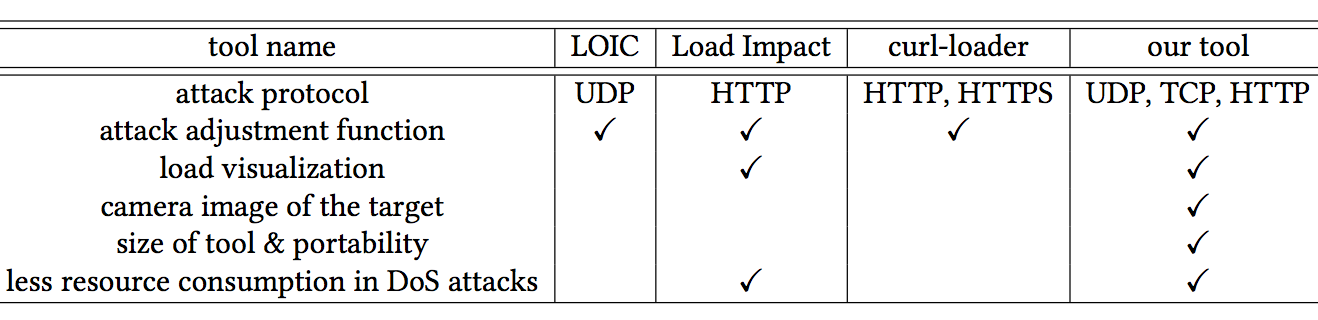
We implemented a portable denial of service (DoS) test tool based on the Mirai malware and conducted a DoS test on several IoT devices. The tool visualizes the load, and adjusts the volume of the attack packet manually. These functionalities enable visual checks of the state of a DoS attack. We can also change the attack method and its performance in different target devices. By applying the tool, we can check the vulnerability of an IoT device and understand the state of the actual DoS attack.
The embedded board offers the following three advantages:
- the resources of the monitor PC need not be devoted to stress testing,
- the compact size saves power and is suitable for carrying,
- the embedded board can be inexpensively scaled.
- macOS Sierra v.10.12.6
- python 2.7
- docker 17.06.2-ce-mac27
- nvm
- npm
docker ps -a
docker start [Process ID]
docker stop [Process ID]
cd kibana
npm start # development mode
### Terminal 1
python correct_time_server.py
### Terminal 2
python recieve_packet_stats.py
### Terminal 3
python webcam_server.py
### Terminal 4
python ping_server.py
telnet [attacker IP address]
[+] This is the Portable DoS Test Tool.
[+] Command is here.
[+] attack:[type target(s) time flags]
[+] (If you use ? in attack command, you can check help.
Ex:[?],[udp ?],[udp 1.1.1.1 ?])
[+] exit:[exit],[quit]
[+] botcount:[botcount]
root@botnet# ?
Available attack list
ack: ACK flood
greip: GRE IP flood
greeth: GRE Ethernet flood
udpplain: UDP flood with less options. optimized for higher PPS
http: HTTP flood
udp: UDP flood
vse: Valve source engine specific flood
syn: SYN flood
root@botnet# udp ?
Comma delimited list of target prefixes
Ex: 192.168.0.1
Ex: 10.0.0.0/8
Ex: 8.8.8.8,127.0.0.0/29
root@botnet# udp 192.168.0.1 ?
Duration of the attack, in seconds
Up to three duplicate attacks are possible
docker pull docker.elastic.co/elasticsearch/elasticsearch:5.3.0
docker run --rm -it -p 9200:9200 --name elasticsearch -e "http.host=0.0.0.0" -e "transport.host=127.0.0.1" -e "xpack.security.enabled=false" docker.elastic.co/elasticsearch/elasticsearch:5.3.0
git clone git@github.com:ertlnagoya/kibana.git
git checkout dev
nvm install $(cat .node-version) # for nodejs version
npm install # for node module
git clone git@github.com:ertlnagoya/portable-DoS-tool-monitor.git